Here are our advice for a secure and well functioning configuration of beroNet VoIP Gateways:
Secure password
The login data of the beroNet VoIP Gateways are „admin / admin“ at delivery. This information is known and published in our online available documentation, so it is essential to inform you that to increase your security please change your password.
You can create a secure password, for example with this tool: http://passwordsgenerator.net/
Deactivation of bfdetect
bfdetect allows you to identify your beroNet VoIP Gateways in the network and to change the IP settings of these. We recommend to use it only at the beginning and then deactivate it to minimize the possibility of external access.
You can disable the option by setting the option „Disable bfdetect“ in the web interface under „Network Settings“ in menu „Preferences“.
Using an https connection
HTTPS is an important factor in increasing security. To ensure an encrypted connection, also on the LAN side, we recommend using https. Among other security features HTTPS prevents third parties from stealing your access data as soon as you log in. When using self-signed certificates, these must be added to the exceptions in your web browser.
Operating the gateway behind a firewall
The security of a VoIP gateway is increased if it is operated behind a firewall and is only accessible from the LAN. NAT and firewall policies are therefore essential. For example, in an all-IP scenario, forwarding rules should be defined for port 5060 and the RTP port range in the router. Port forwarding should also be defined carefully, so that port 5060 is not the same on the WAN side, for example, because this is the only way to increase security and attacks can only occur on the LAN side.
Configuration of the ACL
The ACL is also an important factor that contributes to increase safety. To be able to reach the gateway from the Internet, the ACL must be configured. Access to the gateway can thus be limited to certain IP addresses.
You can configure the ACL via the web interface in the „Preferences“ menu under „ACL“. The configuration of this security option varies depending on whether the gateway is behind a firewall or not.
Gateway behind a firewall
If the gateway is behind a firewall, it is already very secure and using ACL is not absolutely necessary. However, you can use it to prevent attacks on the LAN side.
The ACL can limit access only to the administrator. In delivery state everyone can access the beroNet VoIP Gateway from the LAN. To restrict the access, simply deactivate the option below.
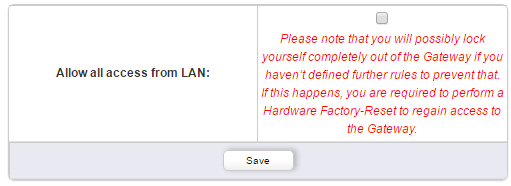
Now only the previously defined IP addresses can reach the device.
Example:
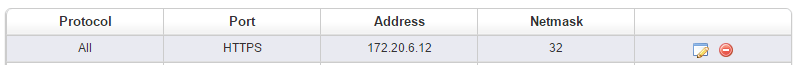
Gateway without firewall
If your beroNet VoIP Gateway is directly accessible from the Internet, we strongly recommend to use the ACL to limit access to your device. The motto should be that only what has to be open to the outside is open to the outside.
In theory only the SIP port or SIP-TLS should be open and the rest should not. The configuration of the ACL could look like this:
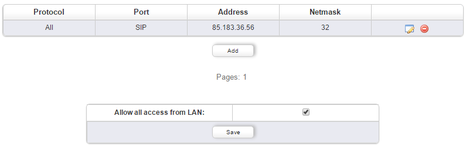
Deactivation of SSH
SSH is not activated in the delivery state. However, the beroNet support might ask for SSH access to the gateway in some cases. However, after successful support SSH should be deactivated again. You can enable and disable SSH via the web interface under „Security“ in the menu „Preferences“.
Changing the default SIP port
To further increase the security we recommend to change the standard SIP port 5060 in the beroNet VoIP Gateway to another port. You can change the “Bind Port” under „SIP Stacks“ in the „SIP“ menu of the web interface:
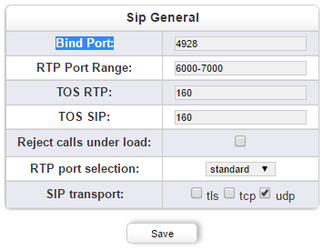
Remember that you have made this change when you set your NAT policies!




